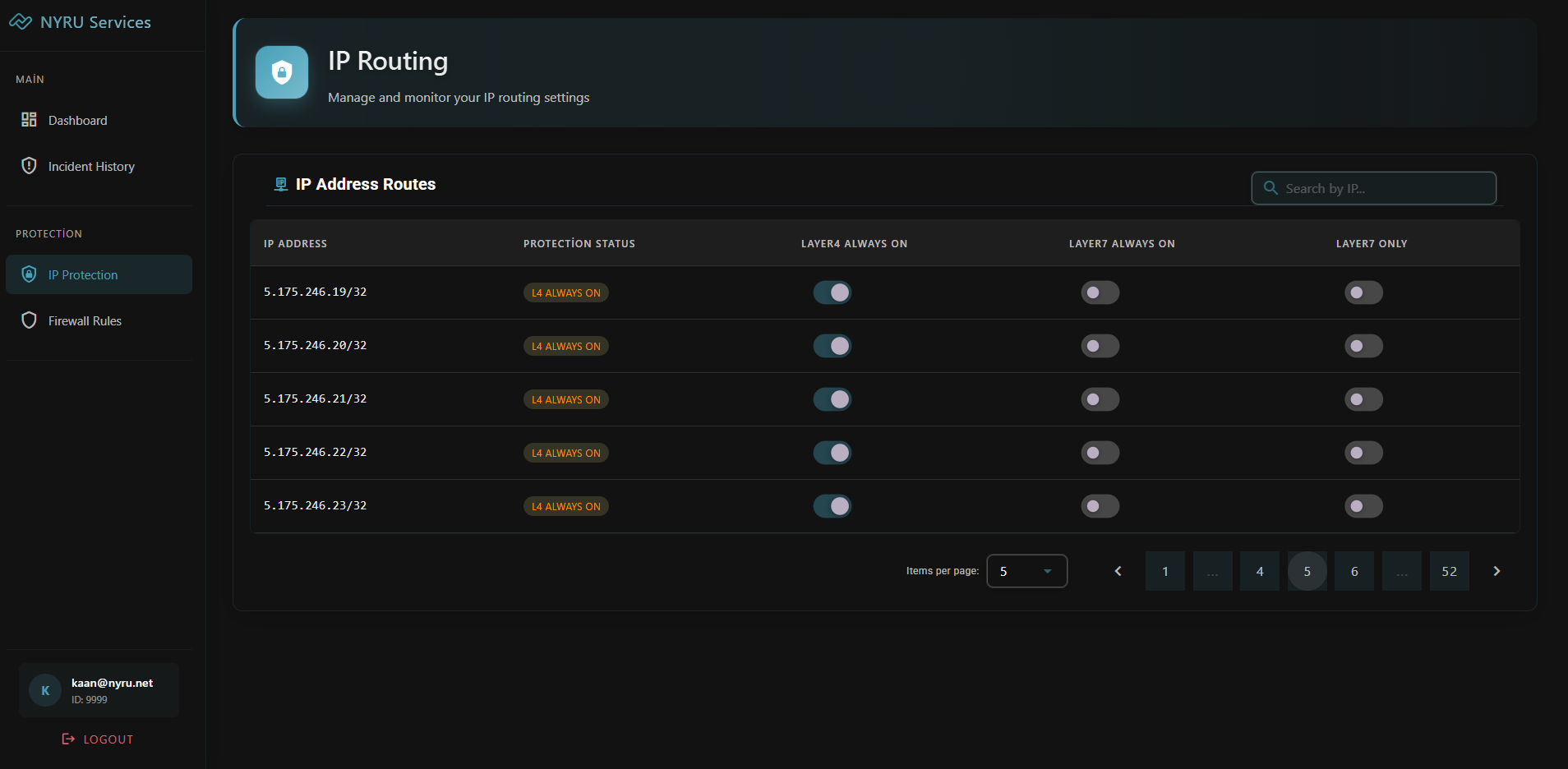
Skip to main contentLayer 4 Protection Modes
Layer 4 protection focuses on network protocol-level attacks (TCP, UDP, ICMP) and offers two operating modes:
Sensor Mode
- Reactive Protection: Activates full mitigation only when an attack is detected
- Low Latency: Minimal impact on normal traffic during peacetime
- Quick Response: Automatically engages filtering within 5 seconds of attack detection
- Resource Efficient: Optimal for services sensitive to latency
- Smart Recovery: Gradually returns to normal operation after attack subsides
Always-On Mode
- Proactive Protection: Continuously filters all incoming traffic
- Maximum Security: Provides constant scrutiny of network packets
- Immediate Defense: No activation delay since filtering is always active
- Consistent Performance: Maintains steady protection level regardless of traffic patterns
- Advanced Protection: Recommended for critical services or frequent attack targets
Layer 7 Protection Modes
Layer 7 protection targets application-level attacks (HTTP floods, slow loris, etc.) with similar operational options:
Sensor Mode
- Threshold-Based: Activates when abnormal HTTP request patterns are detected (You have to set it via Firewall Panel)
- Browser Validation: Issues challenges only during suspected attacks
- Performance Focused: Minimizes impact on legitimate web visitors
- Rapid Deployment: Full protection engages within seconds of attack detection
- Adaptive Response: Protection intensity scales with attack severity
Always-On Mode
- Continuous Verification: Every request undergoes validation
- Bot Prevention: Consistently blocks automated attack tools
- Deep Inspection: Examines request parameters and behaviors
- Persistent Protection: Maintains defensive posture at all times
- Challenge-Response System: May include CAPTCHAs, JavaScript, Button challenges for suspicious traffic
Configuration via Firewall Panel
All protection modes can be customized through your Firewall Panel:
- Switch between modes with a single click for each protected IP
- Set custom thresholds for Sensor Mode activation
- Configure specific filtering rules for each protection layer
- View real-time effectiveness of your current protection settings
- Save different profiles for various scenarios